How to configure a Sophos UTM for two-factor authentication. How to add two-factor authentication to a Sophos UTM - SSL VPN. How to add Two-factor authentication to Sophos UTM - L2TP VPN. Require 2FA for firewall admin. How to require two-factor authentication for admins on the Sophos UTM. How to Add Two-Factor Authentication to Apache 2.4. IPsec client with 2FA VPN using Sophos UTM RSA SecurID 2FA for Sophos UTM Duo of information on this on Two-Factor - Two-Step Authentication SOLVED Sophos — Duo integrates with can't really do it. Not seeing a lot 2FA for remote access flexible authentication options available Set Up - YouTube would like to incorporate Okta Sophos XG and UTM. Either way, if you’d like to enable 2 FA for logging on to an SSL VPN, it’s a relatively easy task on the Sophos UTM. Follow the below steps to set this up ready for 2 factor authentication. Login to the UTM and go to Remote Access - SSL. Here you’ll need to create a Profile for the VPN, so select ‘New Remote Access profile’. Since October 2019, Multi-factor Authentication is turned on by default for newly created Sophos Central accounts. The customer has the option to not enroll in MFA at the time of Trial Activation. This knowledge base article contains the steps on how to set up Multi-factor Authentication for a Sophos Central user.
Configuring two-factor authentication Two-factor authentication ensures that only users with trusted devices can log on. To provide two-factor authentication, you configure the OTP service. Then, end-users scan tokens and obtain passcodes using Sophos Authenticator.
Two-factor authentication ensures that only users with trusted devices can log on. To provide two-factor authentication, you configure the OTP service. Then, end-users scan tokens and obtain passcodes using Sophos Authenticator.
Objectives
When you complete this unit, you’ll know how to do the following:- Turn on the OTP service and specify settings.
- Scan tokens and obtain passcodes using Sophos Authenticator on the client.
Specify OTP service settings
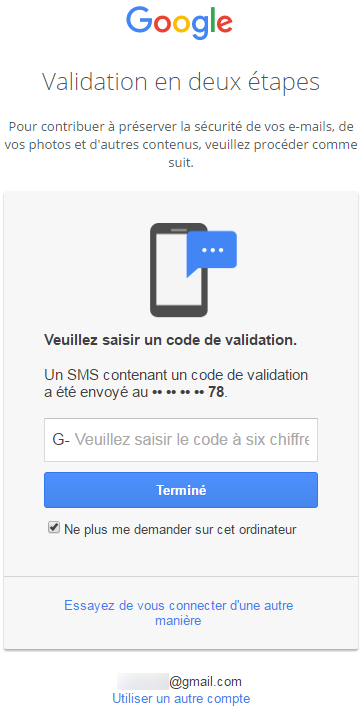
First, you turn on the OTP service. Then, to maximize the protection this type of authentication offers, you require all users to use it. You also specify the features for which two-factor authentication is required.
The following steps are executed on the firewall.
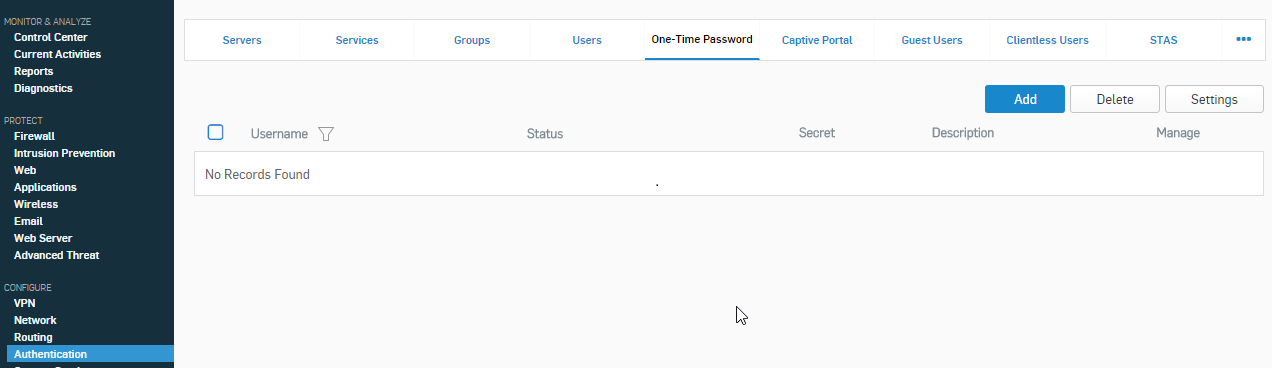
- Go to Authentication > One-time password and click Settings.
- Specify settings.One-time password
On OTP for all users On Auto-create OTP tokens for users On - Enable OTP for WebAdmin and User portal.
- Click Apply.
When you add 2FA to a VPN login you add an extra dimension of security, meaning users may only log on after providing an additional piece of information to prove their identity, in this case a code from Google Authenticator.
This may be something that’s critical in order for your business to comply with industry regulations, or just a feature to give you peace of mind when it comes to the security of your business data. Either way, if you’d like to enable 2 FA for logging on to an SSL VPN, it’s a relatively easy task on the Sophos UTM.
Follow the below steps to set this up ready for 2 factor authentication.
- Login to the UTM and go to Remote Access -> SSL. Here you’ll need to create a Profile for the VPN, so select ‘New Remote Access profile’. If you have integrated your UTM with Active Directory, you can drag ‘Active Directory Users’ into the Users and groups field, otherwise you will need to create users manually and drag the names into the field.
- Next, drag the defined internal network, server or device name into the ‘Local networks’ field. Make sure that ‘Automatic firewall rules’ is ticked and save the profile.
- Next, go to Definitions and Users -> Authentication Services-> One-time Password. Here we will setup the rules for 2 factor authentication. Under ‘Authentication Settings’ we will make changes based on your required setup. Presuming all users will need to authenticate, make sure the following are ticked for the least administration:
- All users must use one-time passwords.
- Auto-create OTP tokens for users
- User Portal
- SSL VPN Remote Access
This will enable all users to login to their UTM portal and view the Google Authenticator barcode on login.
- To enable users to see the Remote Access tab for downloading the VPN Client, go to Management -> User Portal -> Advanced. Under ‘Disable Portal Items’, make sure that ‘Remote Access’ is not ticked.
2fa Sophos Central
Why do we need 2FA?
Found this useful?
Sophos 2fa Software
Beaming is an Internet Service Provider for businesses so we’re experts in networking and all-things connectivity. Subscribe to receive our how-to guides, cyber security advice and business research direct to your inbox once a month.
